Mobile Networking: Protocols, Architectures, and Mechanisms
Indirect TCP (I-TCP)
Two competing insights:
TCP performs poorly together with wireless links;
TCP within the fixed network cannot be changed.
I-TCP segments a TCP connection into a fixed part and a wireless part.
-
I-TCP segments a TCP connection into a
fixed part – Standard TCP is used (between the fixed computer and the access point)
wireless part – optimized TCP protocol
splitting of the TCP connection at, e.g., the foreign agent into 2 TCP connections, no real end-to-end connection any longer
hosts in the fixed part of the net do not notice the characteristics of the wireless part.
The correspondent host in the fixed network does not notice the wireless link .
Socket and state migration after handover of a mobile host
I-TCP requires several actions as soon as a handover takes place.
The access point acts as a proxy buffering packets for retransmission.
After the handover, the old proxy must forward buffered data to the new proxy because it has already acknowledged the data.
Besides buffer content, the sockets of the proxy, too, must migrate to the new foreign agent located in the access point.
The socket reflects the current state of the TCP connection, i.e., sequence number, addresses, ports etc.

Advantages
no changes in the fixed network necessary, no changes for the hosts (TCP protocol) necessary, all current optimizations to TCP still work
transmission errors on the wireless link do not propagate into the fixed network
simple to control, mobile TCP is used only for one hop between, e.g., a foreign agent and mobile host
therefore, a very fast retransmission of packets is possible, the short delay on the mobile hop is known.
Disadvantages
loss of end-to-end semantics, an acknowledgement to a sender does now not any longer mean that a receiver really got a packet, foreign agents might crash.
higher latency possible due to buffering of data within the foreign agent and forwarding to a new FA.
Snooping TCP
One of the drawbacks of I-TCP is the segmentation of the single TCP connection which loses the original end-to-end TCP semantic.
The main function of the enhancement is to buffer data close to the mobile host to perform fast local retransmission in case of packet loss.
The foreign agent buffers all packets with destination mobile host and additionally ‘snoops’ the packet flow in both directions to recognize acknowledgements.
The foreign agent buffers every packet until it receives an acknowledgement from the mobile host.
buffering enable the FA to perform a local retransmission in case of packet loss on the wireless link
Transparent extension of TCP within the foreign agent
buffering of packets sent to the mobile host
lost packets on the wireless link (both directions!) will be retransmitted immediately by the mobile host or foreign agent, respectively (so called “local” retransmission)
the foreign agent therefore “snoops” the packet flow and recognizes acknowledgements in both directions, it also filters ACKs
changes of TCP only within the foreign agent
Data transfer to the mobile host
FA buffers data until it receives ACK of the MH, FA detects packet loss via duplicated ACKs or time-out
fast retransmission possible, transparent for the fixed network
Data transfer from the mobile host
FA detects packet loss on the wireless link via sequence numbers,
FA answers directly with a NACK to the MH
MH can now retransmit data with only a very short delay
GSM mobile services
1) TELE-SERVICES-The abilities of a Bearer Service 1 used by a Teleservice to transport data. These services are further transited in the following ways
voice calls – The most basic Teleservice supported by GSM is telephony. This includes full-rate speech at 13 kbps and emergency calls, where the nearest emergency-service provider is notified by dialing three digits.
Short text message- Short Messaging Service (SMS) service is a text messaging service that allows sending and receiving text messages on your GSM mobile phone. In addition to simple text messages, other text data including news, sports, financial, language, and location-based data can also be transmitted.
2) Bearer- Data services or Bearer Services are used through a GSM phone. to receive and send data is the essential building block leading to widespread mobile Internet access and mobile data transfer. GSM currently has a data transfer rate of 9.6k. New developments that will push up data transfer rates for GSM users are HSCSD (high speed circuit switched data) and GPRS (general packet radio service) are now available.
3) supplementary services – Supplementary services are additional services that are provided in addition to teleservices and bearer services. These services include caller identification, call forwarding, call waiting, multi-party conversations, and barring of outgoing (international) calls, among others. A brief description of supplementary services is given here
MANETs (Mobile Ad hoc Networks)
1. **Dynamic Topology**:
– MANETs are formed by a collection of mobile devices that can move freely and unpredictably.
– The network topology changes frequently as devices move in and out of range, join or leave the network, or adjust their positions relative to each other.
2. **Decentralized Infrastructure**:
– MANETs operate without a fixed infrastructure, such as routers or access points.
– All nodes in the network function as both hosts and routers, relaying data for other nodes as needed.
3. **Limited Resources**:
– Devices in MANETs typically have limited resources in terms of battery power, processing capabilities, and bandwidth.
– Optimizing resource usage and minimizing energy consumption are critical considerations in MANET design.
4. **Dynamic Bandwidth**:
– Bandwidth availability in MANETs fluctuates due to changing network conditions, node mobility, and interference.
– Network protocols and algorithms must adapt to varying bandwidth conditions to ensure efficient data transmission.
5. **Autonomous Operation**:
– MANET nodes operate autonomously without centralized control.
– Each node makes independent decisions regarding routing, data forwarding, and network management.
GSM protocol architecture:
1.Physical Layer: Handles transmission of bits over the air interface using Time Division Multiple Access (TDMA).
2. Data Link Layer: Divided into two sub-layers:
Logical Link Control (LLC): Manages logical channels for user data and signaling.
Medium Access Control (MAC): Controls access to the physical medium, handles channel allocation.
3. Network Layer: Manages routing and addressing, supports mobility management and connection-oriented services.
4. Transport Layer: Provides end-to-end reliable data transfer and flow control.
5.Radio Interface: Interfaces between the mobile station and the base station subsystem.
6. Base Station Subsystem (BSS): Consists of Base Transceiver Station (BTS) and Base Station Controller (BSC), responsible for radio transmission and reception.
7. Network Switching Subsystem (NSS): Core network elements including Mobile Switching Center (MSC), Visitor Location Register (VLR), and Home Location Register (HLR), responsible for call routing, subscriber management, and authentication.
8. Operations and Maintenance Center (OMC): Monitors and manages the GSM network, handles administration, maintenance, and provisioning tasks.

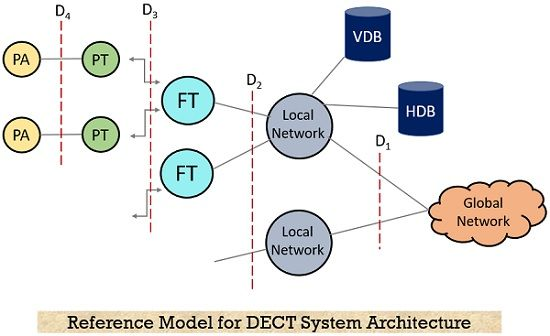
DECT (Digital Enhanced Cordless Telecommunications) system architecture:
1. **Physical Layer**: Utilizes Time Division Duplex (TDD) with adaptive frequency hopping spread spectrum (FHSS) for robust and interference-resistant wireless communication.
2. **Medium Access Control (MAC) Layer**: Manages access to the radio channel, supports multiple users through TDMA (Time Division Multiple Access) and dynamic channel allocation.
3. **Data Link Layer**: Includes Logical Link Control (LLC) and Sublayer Management Entity (SME), responsible for error detection and correction, frame formatting, and quality of service (QoS) management.
4. **Network Layer**: Handles call setup, routing, and mobility management for voice and data services.
5. **DECT Access Point (DAP)**: Acts as a base station, providing connectivity between the DECT system and the Public Switched Telephone Network (PSTN) or Voice over Internet Protocol (VoIP) networks.
6. **Portable Part (PP)**: Handset devices used by end-users, equipped with DECT radio transceivers for wireless communication.
7. **Fixed Part (FP)**: Infrastructure components including base stations (DAPs) and network gateways, responsible for managing call control and interfacing with external networks.
8. **CAT-iq (Cordless Advanced Technology – Internet and Quality)**: An extension to DECT that enables enhanced voice and data services, including high-definition voice and multimedia streaming.
MOBILE IP MECHANISM TO TRANSFER PACKET
1. **Home Agent (HA) and Foreign Agent (FA)**: These are crucial elements in the Mobile IP architecture. The Home Agent maintains the current location of the mobile device and intercepts packets destined for it, while the Foreign Agent assists in routing packets to the mobile device when it’s away from its home network.
2. **Registration**: The process by which the mobile device registers its current Care-of Address (CoA) with its Home Agent allows for seamless packet routing even when the device moves to a foreign network. This registration ensures that the Home Agent knows how to forward packets to the mobile device’s current location.
3. **Tunneling**: The encapsulation of packets by the Home Agent and their subsequent tunneling to the Foreign Agent using the Care-of Address as the destination address is a key mechanism in Mobile IP. Tunneling enables packets to reach the mobile device regardless of its current location, ensuring continuous connectivity as it moves between networks.
difference between route optimization and smooth handoffs
OPERATION OF DHCP
1. **Client Initialization**:
– Client device connects to the network.
– Network interface configured for DHCP.
2. **DHCP Discovery**:
– Client broadcasts DHCP Discover message.
– Message includes client’s MAC address.
– Request for IP configuration information.
3. **DHCP Offer**:
– DHCP servers respond with DHCP Offer.
– Offer contains available IP address, subnet mask, gateway, DNS servers, and lease duration.
4. **DHCP Request**:
– Client selects one DHCP Offer and sends DHCP Request.
– Confirms selection of offered IP address.
5. **DHCP Acknowledgment**:
– DHCP server verifies DHCP Request.
– Sends DHCP Acknowledgment to client.
– Confirms IP address assignment and provides configuration details.
6. **IP Configuration**:
– Client configures network interface with assigned IP address and configuration details.
7. **Lease Renewal**:
– Client attempts to renew lease before expiry.
– Sends DHCP Request to renew lease.
– DHCP server responds with DHCP Acknowledgment and updated lease duration.
8. **Lease Expiry and Release**:
– Lease expires if not renewed.
– IP address released back to DHCP pool.
– Available for assignment to other clients.

