Cybersecurity Fundamentals: Authentication, Encryption & Threats
Message Authentication
Message authentication verifies that a message received over a communication channel is from the legitimate sender and has not been altered during transmission. It ensures data integrity, authenticity, and often non-repudiation (in the case of digital signatures).
Goals of Message Authentication
- Authenticity: Confirms that the message came from the stated sender.
- Integrity: Ensures the message has not been changed.
- Non-repudiation (optional): Prevents the sender from denying having sent the message.
Common Techniques
1. Message Authentication Code (MAC)
- A short piece of information generated using a shared secret key and a cryptographic hash function or block cipher.
- Sent along with the message.
- Receiver uses the same key to verify integrity and authenticity.
2. Digital Signatures
- Use public-key cryptography to sign a message.
- Signature is generated using the sender’s private key.
- Verified using the sender’s public key.
- Provides non-repudiation, i.e., the sender can’t deny sending it.
3. Hash Functions (in combination)
- A message is hashed (e.g., using SHA-256), then the hash is protected via a MAC or digital signature.
Example Scenario (MAC-based)
Alice and Bob share a secret key.
Alice sends:
Message = "Transfer $1000"MAC = HMAC(key, "Transfer $1000")Sent: "Transfer $1000 || MAC"Bob receives the message, recalculates the MAC, and checks it matches.
If yes → message is authenticated.
Understanding Computer Viruses
A virus is a fragment of code embedded in a legitimate program. Viruses are self-replicating and are designed to infect other programs. They can wreak havoc in a system by modifying or destroying files, causing system crashes and program malfunctions. On reaching the target machine, a virus dropper (usually a Trojan horse) inserts the virus into the system.
Types of Computer Viruses
- File Virus: Attaches to program files, alters program start to execute its code first, then returns to the main program. Also called a parasitic virus.
- Boot Sector Virus: Infects the system’s boot sector and runs before the OS loads. Spreads via bootable media like floppy disks.
- Macro Virus: Written in high-level languages like VB; spreads through documents (e.g., Word, Excel) with macros.
- Source Code Virus: Searches and modifies source code files to embed itself and spread further.
- Polymorphic Virus: Changes its code pattern (signature) to evade detection while keeping the same functionality.
- Encrypted Virus: Encrypts its code to hide from antivirus software and includes a decryption routine.
- Stealth Virus: Hides its presence by intercepting system functions and showing uninfected data to users.
- Tunneling Virus: Bypasses antivirus by embedding itself in system-level operations like interrupt handlers.
- Multipartite Virus: Infects multiple components of a system (boot sector, files, memory), making it harder to eliminate.
- Armored Virus: Uses obfuscation techniques (like misleading code location or compression) to resist analysis.
- Browser Hijacker: Alters browser settings, redirects to malicious sites; also called browser redirect virus.
- Memory Resident Virus: Loads into RAM and interferes with system operations, including antivirus programs.
- Direct Action Virus: Activates and replicates only when a specific condition is met, often targeting files listed in AUTOEXEC.BAT.
- Overwrite Virus: Deletes content of infected files, making them partially or fully unusable.
- Directory Virus (File System/Cluster Virus): Modifies file paths in directories, leading to execution of the virus instead of the original file.
- Companion Virus: Creates a similarly named file with a different extension (e.g., Hello.com for Hello.exe) to trick users.
- FAT Virus: Targets the File Allocation Table, potentially corrupting data location info and damaging the storage system.
Security Attacks Explained
Security attacks are actions taken to compromise the confidentiality, integrity, or availability of information or systems. They can be broadly categorized based on how they operate and their goals.
Types of Security Attacks
1. Passive Attacks (Eavesdropping, No Modification)
These attacks aim to intercept or monitor data without altering it.
- Eavesdropping / Sniffing: Monitoring unencrypted network traffic.
- Traffic Analysis: Observing patterns of communication to infer sensitive info.
- 🔸 Goal: Information gathering
- 🔸 Detection: Difficult, as there’s no data alteration
2. Active Attacks (Modification or Disruption)
These involve modifying, deleting, or injecting data.
- Masquerade Attack: Attacker pretends to be someone else.
- Replay Attack: Reuses old valid transmissions to trick the receiver.
- Modification Attack: Alters the contents of the message.
- Denial of Service (DoS): Overwhelms a system to make it unavailable.
- Man-in-the-Middle (MitM): Intercepts and possibly alters communication between two parties.
- 🔸 Goal: Damage, unauthorized access, disruption
- 🔸 Detection: Easier than passive attacks
Other Common Security Attacks
| Attack Type | Description |
|---|---|
| Phishing | Fake messages or sites used to steal credentials or sensitive info |
| Spoofing | Forging IP, MAC, or email to impersonate a trusted source |
| SQL Injection | Malicious SQL queries injected into input fields to access databases |
| Cross-Site Scripting (XSS) | Malicious scripts injected into web pages viewed by users |
| Brute Force Attack | Trying all possible passwords or keys until the correct one is found |
| Ransomware | Encrypts files and demands payment for decryption |
| Zero-Day Attack | Exploits unknown vulnerabilities before they are patched |
Data Encryption Standard (DES) Fundamentals
DES (Data Encryption Standard) is a symmetric encryption algorithm that uses the same key for both encryption and decryption. It processes data in fixed-size blocks of 64 bits using a 56-bit key (8 bits are used for parity, making the full key 64 bits long).
Key Features of DES
- Type: Symmetric block cipher
- Block size: 64 bits
- Key size: 56 bits (actual key used)
- Rounds: 16
- Structure: Feistel network
How DES Works (Simplified Steps)
- Initial Permutation (IP):
The 64-bit plaintext is permuted using a fixed IP table. - Key Generation:
The 56-bit key is divided into two halves.
16 subkeys (48 bits each) are generated for the 16 rounds. - 16 Rounds of Processing: Each round consists of:
- Expansion (from 32 to 48 bits)
- XOR with subkey
- Substitution using S-boxes (to reduce back to 32 bits)
- Permutation
- XOR with left half, then swap halves
- Final Permutation (Inverse IP):
After 16 rounds, the final output goes through an inverse permutation to produce the ciphertext.
DES Encryption & Decryption
- Same algorithm is used for both.
- Subkeys are used in reverse order during decryption.
DES Security Issues
- Vulnerable to brute-force attacks due to small key size (56-bit).
- Modern computers can break DES in hours or less.
- Replaced by Triple DES (3DES) and AES in most applications.
Applications of DES
- Data encryption in legacy systems
- ATM PIN encryption
- File encryption (historically)
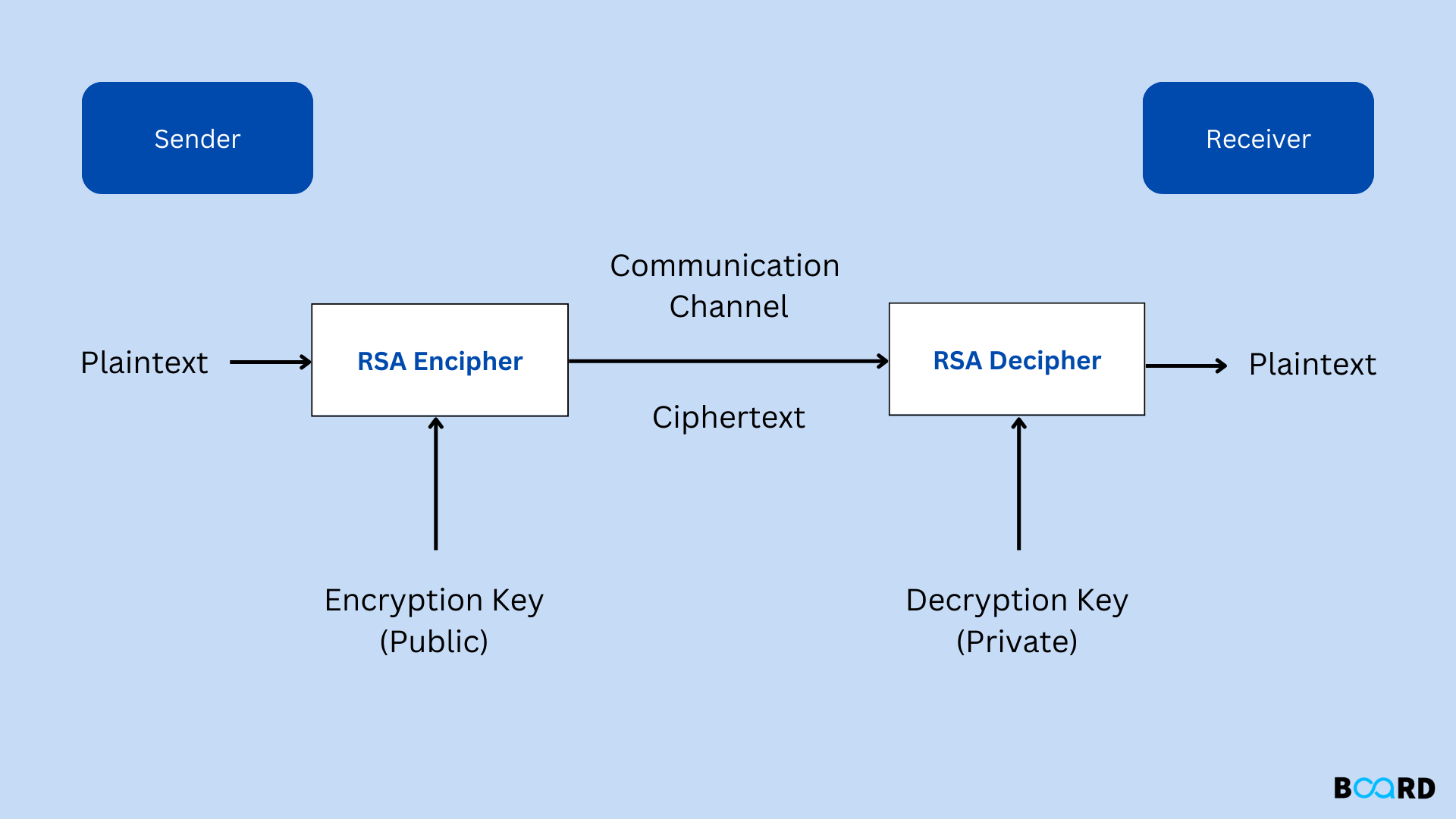
RSA Algorithm: Public-Key Cryptography
RSA (Rivest-Shamir-Adleman) Algorithm is an asymmetric or public-key cryptography algorithm, which means it works on two different keys: Public Key and Private Key. The Public Key is used for encryption and is known to everyone, while the Private Key is used for decryption and must be kept secret by the receiver.
RSA Algorithm is based on factorization of large numbers and modular arithmetic for encrypting and decrypting data. It consists of three main stages:
RSA Algorithm Stages
- Key Generation: Creating Public and Private Keys
- Encryption: Sender encrypts the data using Public Key to get ciphertext.
- Decryption: Decrypting the ciphertext using Private Key to get the original data.
| Advantages | Disadvantages |
|---|---|
| Provides strong security | Slower than symmetric encryption (e.g., AES) |
| Enables secure key exchange | Requires large keys for strong security |
| Supports digital signatures | Not suitable for encrypting large data |
| Public key can be shared openly | Key generation and encryption are resource-intensive |
| Widely adopted and trusted | Vulnerable if poor random primes are chosen |
Diffie-Hellman (DH) Key Exchange
Diffie–Hellman (DH) is a key exchange algorithm that allows two parties to securely generate a shared secret key over an insecure channel. It is based on the discrete logarithm problem and is widely used in secure communication protocols like TLS, SSH, and VPNs.
How Diffie-Hellman Works (Simplified)
- Publicly agree on a prime number
pand baseg. - Each party selects a private key:
- Alice: private key
a→ computesA = g^a mod p - Bob: private key
b→ computesB = g^b mod p
- Alice: private key
- Exchange public values
AandB. - Each computes the shared key:
- Alice:
S = B^a mod p - Bob:
S = A^b mod p
- Alice:
Both arrive at the same shared secret S.
| Advantages | Disadvantages |
|---|---|
| Secure key exchange over public networks | Vulnerable to Man-in-the-Middle (MitM) attacks |
| Simple and efficient | No authentication or encryption built-in |
| Based on hard mathematical problems | Requires large primes for strong security |
Trusted Systems in Cybersecurity
Trusted systems are special systems designed to serve the purpose of providing security. Safety is ensured by trusted systems by protecting the system against malicious software and third-party intruders. Trusted systems allow only verified users to access the computer system. Trusted systems are responsible for providing security at different levels and based on different parameters.
Key Features of a Trusted System
- 1. Access Control – Ensures only authorized users can access specific data or resources.
- 2. Authentication – Verifies the identity of users or systems.
- 3. Audit Trails – Keeps logs of system activities for monitoring and investigation.
- 4. Data Integrity – Prevents unauthorized modification of data.
- 5. Security Policy Enforcement – Enforces strict rules as per organizational needs.
Main Components of Trusted Systems
- 1. Trusted Computing Base (TCB) – Core part of the system responsible for enforcing security.
- 2. Security Kernel – Enforces low-level security mechanisms like access control.
- 3. Reference Monitor – A theoretical component that controls all access to system resources.
Example Use Cases for Trusted Systems
- Military and government systems
- Banking and financial institutions
- Hospitals and research organizations
Advantages & Disadvantages of Trusted Systems
| Advantages | Disadvantages |
|---|---|
| High security and policy enforcement | Complex and costly to develop |
| Prevents unauthorized access effectively | Can be harder to upgrade or customize |
| Ideal for sensitive environments | May affect system performance |
